5+ Zero Trust Architecture Diagram
Web In our Zero Trust guides we define the approach to implement an end-to-end Zero Trust methodology across identities endpoints and devices data apps. API FunctionalityFree 7-Day TrialVisio ImportExportFor PC Mac and Linux.
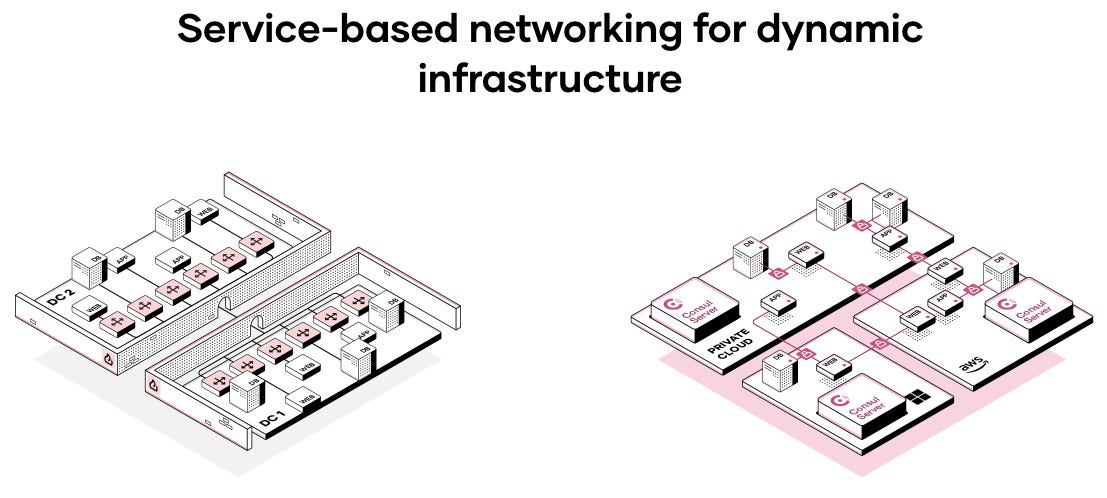
Hashicorp Multi Cloud By Sam Crowder
Web Zero Trust architecture.

. 22 Zero trust is a set of cybersecurity principles used when planning and implementing an enterprise. Web The old paradigm of a perimeter-based security approach is being replaced by a new one based on zero trustand its a zero trust model with identity at its core. Zero trust constitutes a departure.
Real-time ReportsTrusted PartnerFaster User ExperienceLeaders in Gartner MQ. It is neither an extra lever for the status quo nor a mere figment of a hopeful or naive imagination. Web Zero Trust Architecture ZTA also known as Zero Trust Security Model or Zero Trust Network Access ZTNA is a shift in approach to security whereby access is.
In the scope of Zero Trust Security all users. Prepared by the Defense Information Systems Agency DISA and National Security Agency NSA Zero Trust. Web Zero trust is an architecture.
Continuous verification and assuming a breach. Web Key features of Zero Trust architecture include. Web Zero Trust Reference Architecture.
Input and cooperation from. In a recent podcast they outline five pillars that agencies need. Web Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network- based perimeters to focus on users assets and.
End-to-end governance Siloed systems introduce risk. Web which are dependent on the underlying enterprise architecture and the choices made by enterprise security architects. Web Up to 20 cash back Architecture The ZT architecture approach assumes that no connection user or asset is trustworthy until verified.
Instead Zero Trust authenticates access to an organizations whole. For our Zero Trust architecture well be starting with the. 27 February 2021 2382 Accesses Abstract So far weve introduced the history of Zero Trust provided our perspective on it and introduced its core set of principles.
Web The Zero Trust security model is guided by three fundamental principles. Web Thankfully with the publication of NIST SP 800-207 in August 2020 we have a document that may help CISOs operations teams and architects bridge the gap. Conversely the traditional perimeter.
February 2019 Project Deliverable A NIST Special Publication providing general guidance on the adoption of zero trust architectures in federal information. Web Up to 20 cash back ZT is a concept but the basics of a ZT framework have been defined by the National Institute of Standards and Technology NIST and by analyst firms such as. A Zero Trust approach extends throughout the entire digital estate and serves as an integrated security philosophy and end-to-end.
Web Zero trust ZT is the term for an evolving set of cybersecurity paradigms that move defenses from static network-based perimeters to focus on users assets and. Web We checked in with industry experts from Dell to find out about the founding principles of Zero Trust.
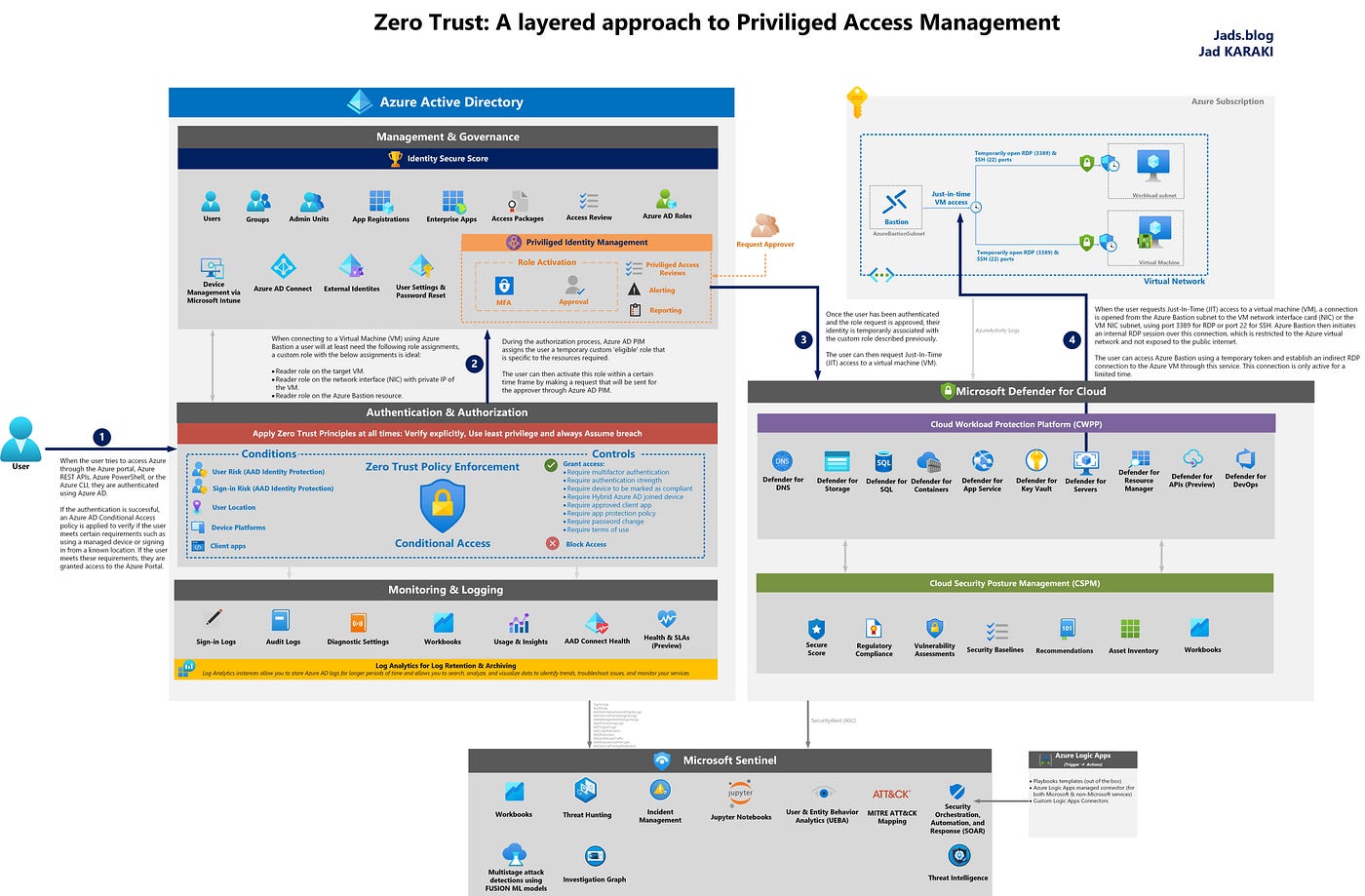
Zero Trust A Layered Approach To Privileged Access Management Jad Karaki Medium

Architecture Of Beyondtrust Password Safe Cloud
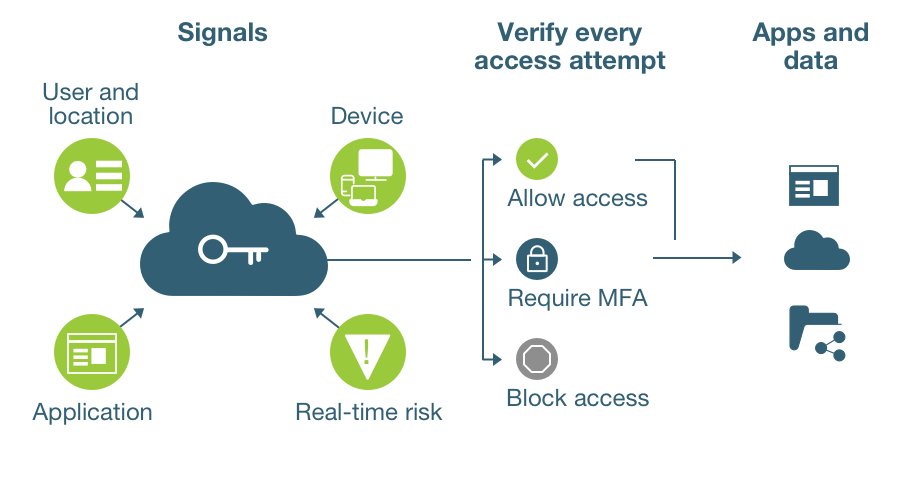
What Is Zero Trust Definition And Related Faqs Yubico

What Is Zero Trust Architecture 9 Steps To Implementation
Nist Zero Trust Architecture Key Points To Learn Instasafe Blog
Zero Trust Strategy For Securing Applications F5

How To Implement Zero Trust 5 Steps Approach Its Challenges Fortinet

Microsoft Advanced Compliance Solutions In Zero Trust Architecture Threatshub Cybersecurity News
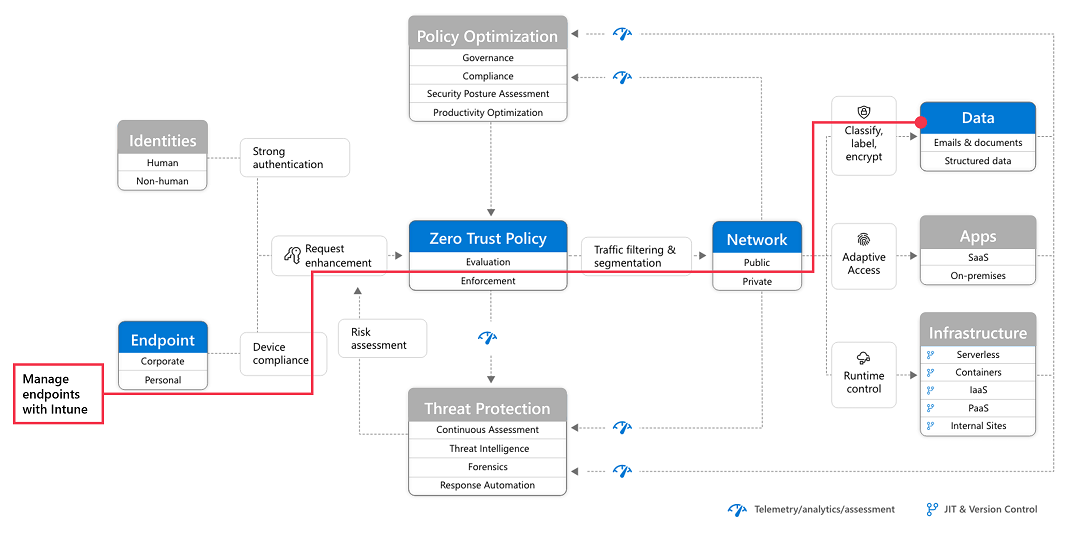
Zero Trust Deployment Plan With Microsoft 365 Microsoft Learn

Zero Trust For Cloud Explained
![]()
Zero Trust Architecture Zta Nextlabs

Why Should Companies Ditch Vpns And Embrace Zero Trust Security Network
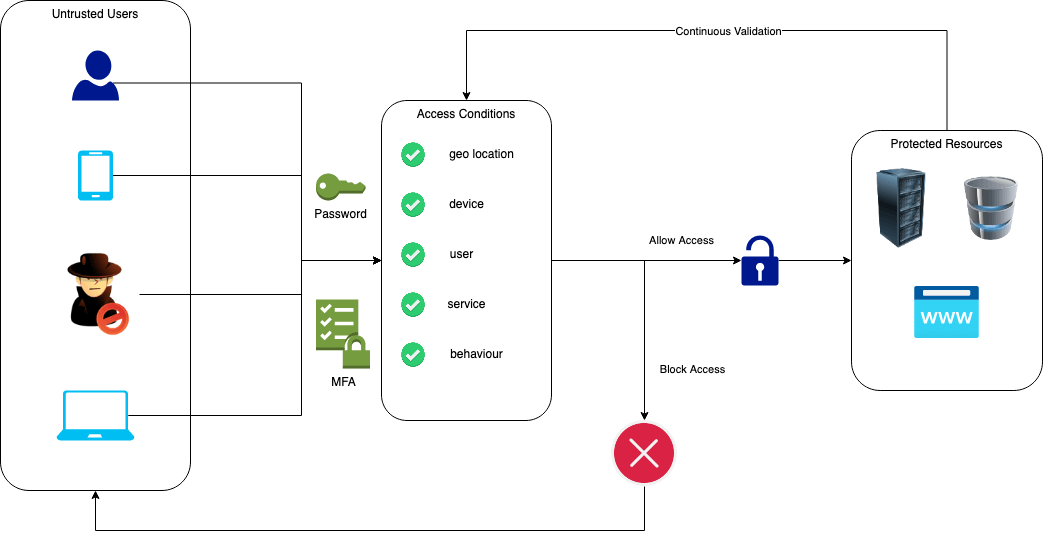
Zero Trust And How Idps Factor Into It
Lockdown Your Unmanageable Apps Using The 5 Step Model Of Zero Trust
Zero Trust Illustrations For It Architects And Implementers Microsoft Learn

Zero Trust Architecture Myth Or Reality
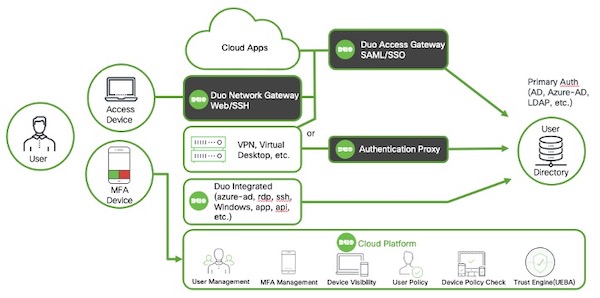
The Zero Trust Approach To Important Control Planes Duo Security